How to Check Opened Port on Linux VPS Server using SSH command
What is a Listening Port on a Linux Server
Services and applications use listening ports to monitor incoming network requests. Each listening port has an interaction protocol (TCP or UDP) and an IP address.
Listening ports may be open or closed depending on the system and network configuration.
When an external connection uses the appropriate protocol, open ports on the system accept it.
Port numbers below 1000 are usually reserved for system services (for instance, port 80 for HTTP). Additional services initiated by other applications are assigned an available port number. In most cases, the system admin needs to alter the firewall rules to allow traffic to open ports.
Steps to check opened ports on a Linux VPS server
In the Linux operating system, the “netstat” command can be used to check the opened ports on a VPS (Virtual Private Server) server. Opened ports are important to identify because they are a gateway for incoming and outgoing traffic to the server. Sometimes, the server’s firewall or other configuration can prevent traffic from reaching the intended port, leading to service disruptions or unexpected results. Checking opened ports can help diagnose these issues and ensure that the server is functioning as intended. In this guide, we will go through the steps to check opened ports on a Linux VPS server.
Step 1: Connect to the VPS server
Before we can check the opened ports, we need to connect to the VPS server. This can be done using an SSH (Secure Shell) client. On a Mac or Linux machine, you can use the built-in terminal application. On Windows, you can use a third-party application like PuTTY. To connect, open the terminal application and enter the following command, replacing “server_ip_address” with the IP address of your VPS server:
ssh root@server_ip_address
 You will be prompted to enter the password for the root user. Enter the password and press Enter.
You will be prompted to enter the password for the root user. Enter the password and press Enter.
Step 2: Check the opened ports
Once connected to the VPS server, we can use the “netstat” command to check the opened ports. Enter the following command:
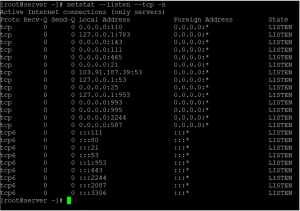
netstat --listen --tcp -n
This command will display a list of all opened TCP ports on the server that are actively listening for incoming connections. The –listen option specifies that we want to see only the sockets that are in listening mode, and the –tcp option specifies that we want to see only the TCP sockets. The -n option specifies that we want to see the numerical addresses instead of service names.
alternatively, type:
netstat -tuln
This command will display a list of all opened ports on the server. The “-tuln” options specify that we want to see the list of TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) ports with numerical addresses instead of service names.
Step 3: Interpret the results
The output of the “netstat” command will display a list of all opened ports on the server with the following information:
“Proto”: the protocol used by the port (TCP or UDP)
“Recv-Q” and “Send-Q”: the amount of data waiting to be received and sent
“Local Address”: the IP address and port number of the server
“Foreign Address”: the IP address and port number of the client
“State”: the current state of the connection (e.g., “LISTEN” for waiting for incoming connections)
Make sure to look for the ports that you are interested in, such as the ports used by a specific service or application.
[root@vps-server ~]# netstat --listen --tcp -n
Commands Mentioned:
- ssh– connect to a remote server using the Secure Shell protocol
- netstat– display network connections, routing tables, and network interface statistics
Common port blocks and their significance
Blocks help in controlling the flow of data through specific ports. This is critical because it regulates traffic and prevents unauthorized access or malicious activities over the internet.
Internet service providers (ISPs) take this preemptive measure to safeguard against potential threats and maintain the integrity and confidentiality of any sensitive data and information transmitted. They may also restrict access to certain applications or services to comply with legal or regulatory requirements by blocking the ports they use.
For instance, they might block the ports commonly employed by peer-to-peer file-sharing applications to discourage users from using these services to illegally download copyrighted content to guarantee a fair and lawful use of their network resources.
Now, let's take a look at some common port blocks and their significance in maintaining a secure network environment:
- Port 21 (FTP) – File Transfer Protocol (FTP) is commonly used for transferring files over a network. However, leaving this port unrestricted can expose systems to potential security risks.
- Port 22 (SSH) – Secure Shell (SSH) is widely used for secure remote administration of systems. Blocking port 22, or restricting SSH access to trusted IP addresses, adds an extra layer of protection and reduces the likelihood of unauthorized intrusions.
- Port 25 (SMTP) – The Simple Mail Transfer Protocol (SMTP) port handles email transmission. Port 25 blocking is often implemented to prevent the abuse of email servers for spamming purposes, which can help organizations curtail the potential for unauthorized mass email campaigns and reduce the risk of falling victim to email-related security threats.
- Port 80 (HTTP) – Port 80 is used for unencrypted web traffic using the Hypertext Transfer Protocol (HTTP). While it is essential for web browsing, it can be an entry point for various cyberattacks. Blocking this port will force users to access websites through encrypted connections like Hypertext Transfer Protocol Secure (HTTPS) on port 443, which enhances data privacy and security.
- Port 110 (POP3) – The Post Office Protocol version 3 (POP3) port retrieves emails from a remote server. Blocking this port helps protect against unauthorized access to email accounts and prevents potential data breaches or unauthorized retrieval of sensitive information. Instead, consider using port 995 for the Post Office Protocol 3 over SSL (POP3S).
- Port 143 (IMAP) – The Internet Message Access Protocol (IMAP) port is another protocol used for email retrieval that is best blocked. It is recommended to use SSl/TLS with IMAP to ensure the protection of email communications.
