cPHulk – In the age of constant cyber threats, server security is more crucial than ever. Cybercriminals are increasingly using brute-force attacks to gain unauthorized access to servers, exploiting weak or commonly used passwords to infiltrate systems. This is where cPHulk Brute Force Protection comes into play. For anyone managing a server with cPanel & WHM, cPHulk provides an essential layer of defense by actively protecting against these types of attacks.
In this post, we’ll explore what cPHulk is, how it works, and why it’s a must-have tool for anyone serious about server security.
What is cPHulk?
cPHulk is a security feature included in cPanel & WHM, specifically designed to protect your server from brute-force attacks. These attacks involve automated attempts to guess usernames and passwords until the correct combination is found, which can lead to unauthorized access and potentially devastating data breaches.
With cPHulk, you can set up rules that monitor login attempts across services like SSH, FTP, and even webmail, blocking repeated failed attempts and preventing attackers from brute-forcing their way into your server. This provides peace of mind, knowing that there is a powerful, built-in tool actively monitoring for suspicious activity and responding to it in real time.
Why Do You Need cPHulk for Server Security?
Brute-force attacks are one of the most common and simplest forms of attack, but they can be very effective if a server isn’t properly protected. Here’s why cPHulk is crucial for safeguarding your server:
1. Real-Time Monitoring and Blocking of Unauthorized Access Attempts
cPHulk actively monitors login attempts to detect patterns that resemble brute-force attacks. If someone (or something) tries to log in with incorrect credentials too many times, cPHulk can block them automatically. This prevents attackers from overwhelming your server with repeated login attempts and significantly reduces the risk of unauthorized access.
2. Customizable Settings for Targeted Protection
One of cPHulk’s strengths is its configurability. You can set thresholds for blocking IP addresses, usernames, or entire countries based on the number of failed login attempts. This means you can tailor cPHulk’s protection to fit the specific needs of your server and security policies, making it more flexible than static security measures.
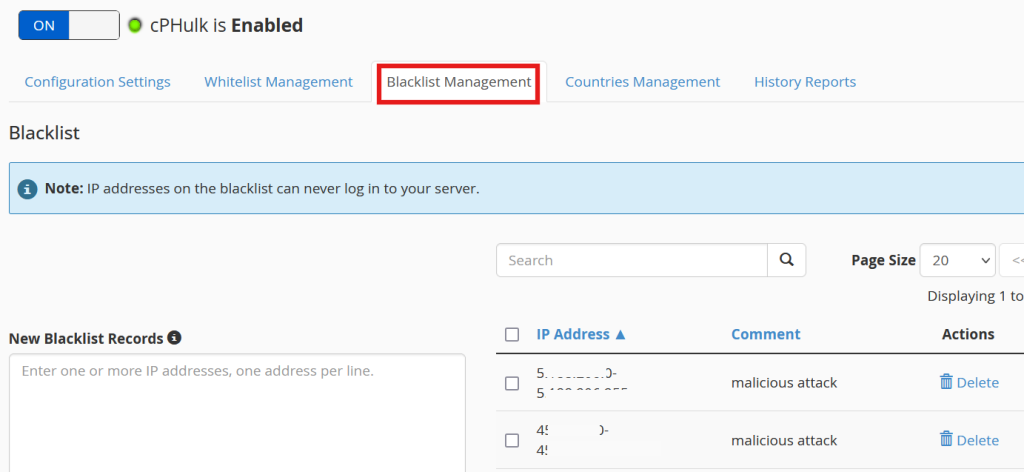
3. Blacklist and Whitelist Functionality
With cPHulk, you can maintain blacklists for IP addresses or geographic locations that you want to block permanently. Alternatively, you can use whitelists to ensure certain IP addresses or users are never blocked, even if they trigger security thresholds. This level of control helps reduce the risk of blocking legitimate users while still keeping threats at bay.
4. Detailed Login History Reports
cPHulk includes reporting tools that allow you to track login attempts and monitor for suspicious activity. This feature helps administrators review patterns over time and identify potentially malicious users or IP addresses that frequently trigger brute-force warnings. Understanding these patterns can help you refine your security settings to prevent future attacks.
5. Minimizes Downtime and Server Resource Drain
Brute-force attacks are not only a security risk but can also drain server resources, slowing down performance and, in extreme cases, leading to downtime. By blocking malicious IPs early, cPHulk helps your server run more efficiently and reduces the chances of performance issues.
Key Features of cPHulk
Here are some of the standout features that make cPHulk such a valuable asset for server security:
- Automatic IP Blocking: Instantly block IP addresses or IP ranges after a specified number of failed login attempts.
- User-Based Protection: Block access based on repeated failed login attempts by a specific user, regardless of the IP address.
- Country-Based Blocking: If you frequently encounter attacks from specific regions, you can set up country-based blocking to enhance security.
- Smart User Lockout: Configure lockout periods based on failed login thresholds to prevent accidental lockouts of valid users.
- Integration with cPanel & WHM: Since cPHulk is part of cPanel & WHM, you can manage all settings directly from your control panel without the need for additional software.
How to Get Started with cPHulk
Enabling and configuring cPHulk is straightforward:
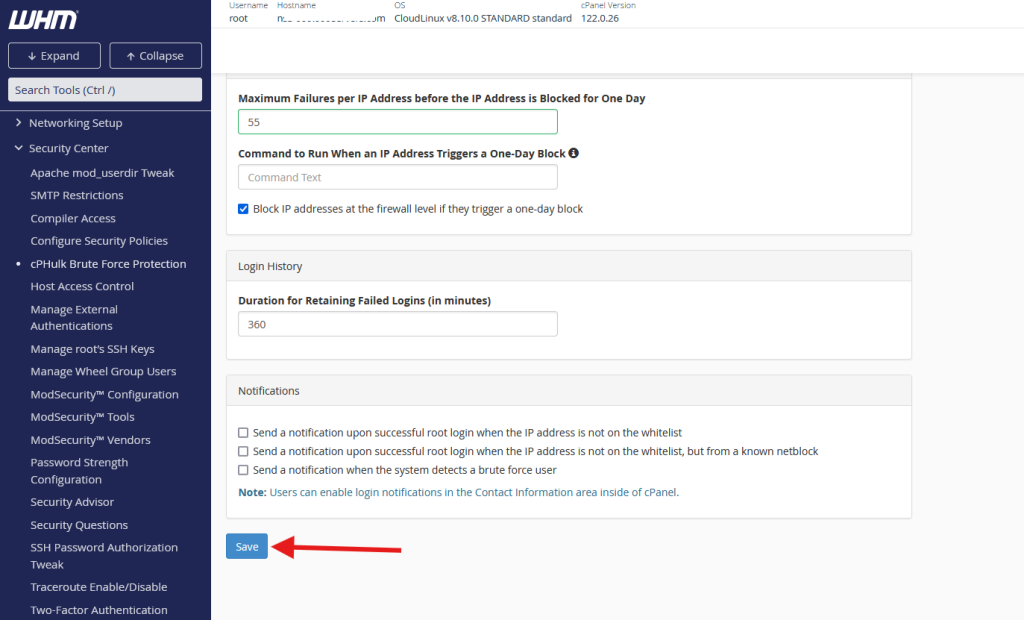
Step 1: Log into WHM (Login credentials provided by hosting server provider) and navigate to the Security Center

Step 2: Click on cPHulk Brute Force Protection.
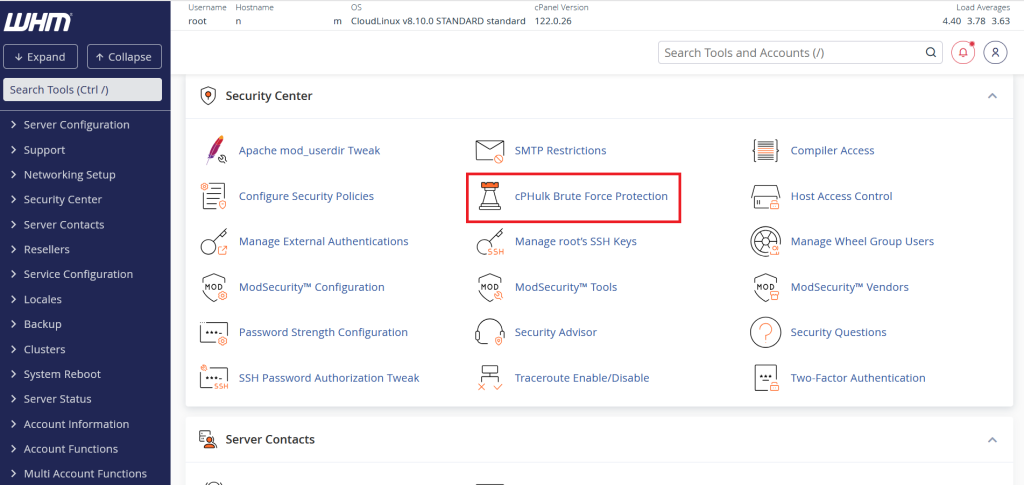
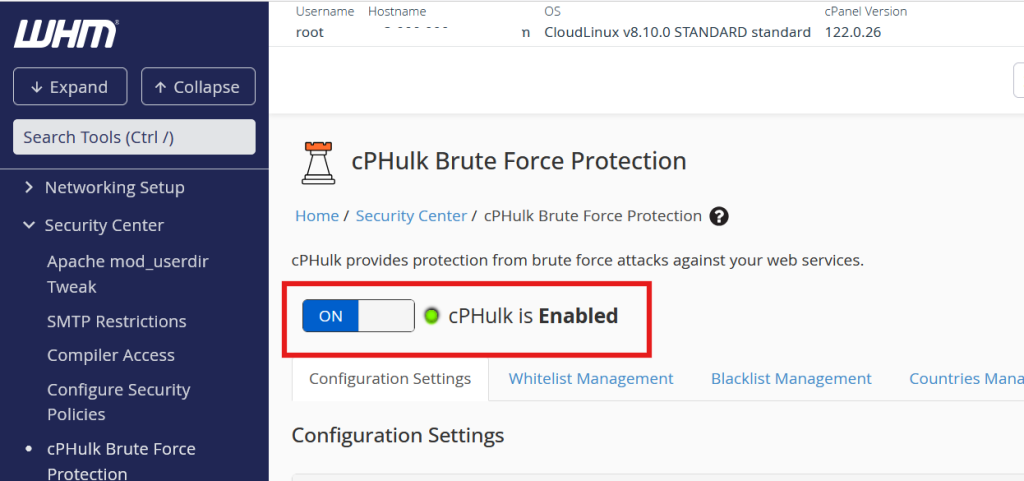
Step 3: Enable cPHulk by selecting the option to turn it on.
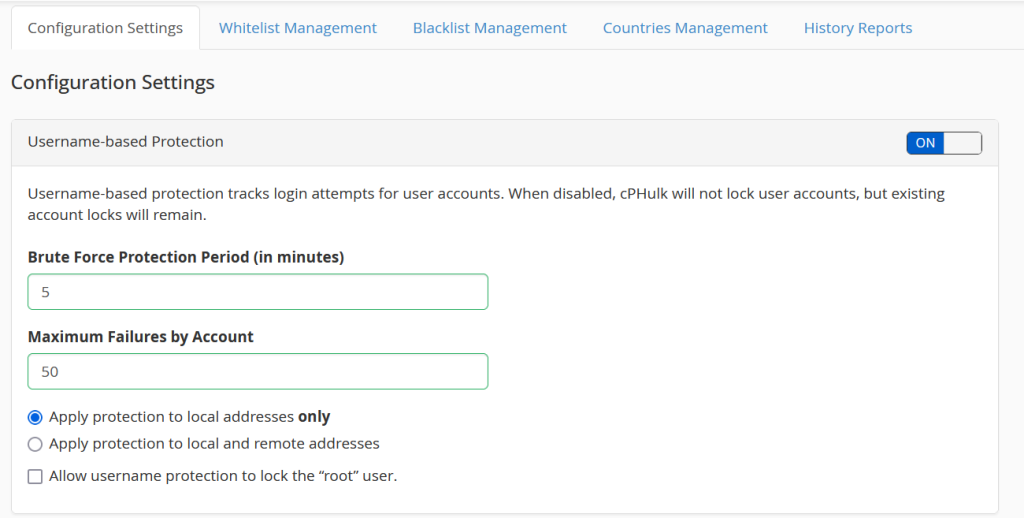
Step 4: Set your thresholds for failed logins (e.g., after 5 failed attempts, block the IP).
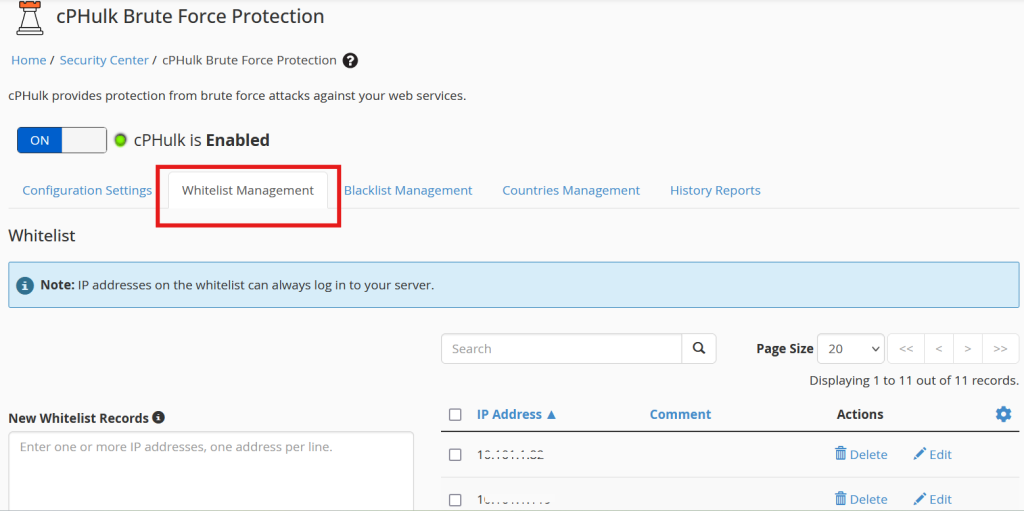
Step 5: Configure blacklists and whitelists as needed for specific IP addresses.
Step 6: Save your settings, and cPHulk will immediately begin protecting your server.
In Summary
cPHulk Brute Force Protection is an indispensable tool for any server administrator using cPanel & WHM. By providing real-time monitoring, IP blocking, user-based lockouts, and detailed reports, cPHulk acts as a robust line of defense against brute-force attacks. It’s customizable, easy to manage, and a powerful way to keep your server secure while ensuring that only legitimate users gain access.
Investing a little time in setting up and understanding cPHulk can save you from the far-reaching consequences of a security breach. Whether you’re managing a small personal server or an enterprise-level setup, cPHulk can be a game-changer in your security strategy.

